01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. "{\"accountId\": \"617755838952421242\",\"accountName\": \"CORP\",\"activityType\": 90,\"agentId\": \"1109290742018175361\",\"agentUpdatedVersion\": null,\"comments\": null,\"createdAt\": \"2021-03-11T12:42:56.308213Z\",\"data\": { \"accountName\": \"CORP\", \"computerName\": \"debian-SentinelOne\", \"createdAt\": \"2021-03-11T12:42:56.297860Z\", \"fullScopeDetails\": \"Group Default Group in Site Sekoia.io of Account CORP\", \"groupName\": \"Default Group\", \"scopeLevel\": \"Group\", \"scopeName\": \"Default Group\", \"siteName\": \"Sekoia.io\", \"status\": \"started\"},\"description\": null,\"groupId\": \"1107851598374945694\",\"groupName\": \"Default Group\",\"hash\": null,\"id\": \"1109290868249950294\",\"osFamily\": null,\"primaryDescription\": \"Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC.\",\"secondaryDescription\": null,\"siteId\": \"1107851598358168475\",\"siteName\": \"Sekoia.io\",\"threatId\": null,\"updatedAt\": \"2021-03-11T12:42:56.301271Z\",\"userId\": null}", "Agent debian-SentinelOne started full disk scan at Thu, 11 Mar 2021, 12:42:56 UTC. Attacker might want to abuse ptrace functionnality to analyse memory process. In details, the following table denotes the type of events produced by this integration. When a threat is detected in SentinelOne, SentinelOne StorylineTM correlates detections and activity data across security layers, including email, endpoints, mobile, and cloud. ; Next to API Token, click Generate. Detects Arbitrary File Read, which can be used with other vulnerabilities as a mean to obtain outputs generated by attackers, or sensitive data. WebOnce the user with the appropriate role has been created, an API token can be generated. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. Our goal at Scalyr is to provide sysadmins and DevOps engineers with a single log monitoring tool that replaces the hodgepodge of  Skuteczne rzucanie granatw podczas skoku. These tools often use the socks5 commandline argument, however socks4 can sometimes be used as well. As described by Microsoft, this behavior is unique and easily identifiable due to the use of folders named with underscores "__" and the PE name "DriveMgr.exe".
Skuteczne rzucanie granatw podczas skoku. These tools often use the socks5 commandline argument, however socks4 can sometimes be used as well. As described by Microsoft, this behavior is unique and easily identifiable due to the use of folders named with underscores "__" and the PE name "DriveMgr.exe".  WebIdentify, contain, respond, and stop malicious activity on endpoints SIEM Centralize threat visibility and analysis, backed by cutting-edge threat intelligence Risk Assessment & Vulnerability Management Identify unknown cyber risks and routinely scan for vulnerabilities Identity Management This detection rule doesn't match Sysmon EventID 1 because the user SID is always set to S-1-5-18. Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378. Detects attempts to deactivate/disable Windows Defender through base64 encoded PowerShell command line. Create and follow support cases. The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. Detection of impacket's wmiexec example, used by attackers to execute commands remotely. Detects various Follina vulnerability exploitation techniques. This is based on the Compatability Troubleshooter which is abused to do code execution. WebSentinelOne currently offers the following integrations: SentinelOne kann durch Syslog-Feeds oder ber unsere API problemlos mit Datenanalyse-Tools wie SIEM integriert
WebIdentify, contain, respond, and stop malicious activity on endpoints SIEM Centralize threat visibility and analysis, backed by cutting-edge threat intelligence Risk Assessment & Vulnerability Management Identify unknown cyber risks and routinely scan for vulnerabilities Identity Management This detection rule doesn't match Sysmon EventID 1 because the user SID is always set to S-1-5-18. Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378. Detects attempts to deactivate/disable Windows Defender through base64 encoded PowerShell command line. Create and follow support cases. The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. Detection of impacket's wmiexec example, used by attackers to execute commands remotely. Detects various Follina vulnerability exploitation techniques. This is based on the Compatability Troubleshooter which is abused to do code execution. WebSentinelOne currently offers the following integrations: SentinelOne kann durch Syslog-Feeds oder ber unsere API problemlos mit Datenanalyse-Tools wie SIEM integriert  The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. 01 - Prod\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Documentation. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. It could be used to retrieve informations or to be abused for persistence.
The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. 01 - Prod\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Documentation. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. It could be used to retrieve informations or to be abused for persistence.  Reason why this event happened, according to the source. It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); 2015-2022 Gametip.pl | Polityka Prywatnoci | Wsppraca. $ 4. Detects rare taskkill command being used. Show me the third-party integrations you've already built yourself and tell me where to get them. ", "This binary imports functions used to raise kernel exceptions. Detects specific process executable path used by the Phorpiex botnet to masquerade its system process network activity.
Reason why this event happened, according to the source. It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); 2015-2022 Gametip.pl | Polityka Prywatnoci | Wsppraca. $ 4. Detects rare taskkill command being used. Show me the third-party integrations you've already built yourself and tell me where to get them. ", "This binary imports functions used to raise kernel exceptions. Detects specific process executable path used by the Phorpiex botnet to masquerade its system process network activity. 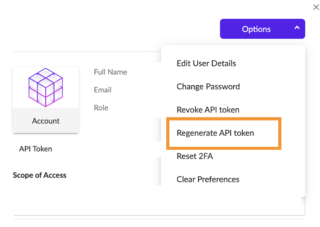 Full path to the file, including the file name. Detects suspicious icacls command granting access to all, used by the ransomware Ryuk to delete every access-based restrictions on files and directories. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Jak wczy auto bunnyhop? Detects Koadic payload using MSHTML module, Detects different loaders used by the Lazarus Group APT. Your most sensitive data lives on the endpoint and Note The name of the scheduled task used by these malware is very specific (Updates/randomstring). Komenda na legalnego aimbota CS:GO. Detects command lines with suspicious args, Detects specific commands used regularly by ransomwares to stop services or remove backups, Detects the malicious use of a control panel item. WebStep 1: Configure SentinelOne to allow API access to runZero Log in to SentinelOne with the account being used for the runZero integration. You do not need to create a new account. Detects command used to start a Simple HTTP server in Python. Detect a basic execution of PowerCat. Najlepsze komendy na FPS CS GO, Komenda na WH CS GO | Legalny wallhack w Counter Strike. Through the sharing of intelligence from email and endpoint security solutions, analysts obtain increased visibility and context into threats that would not be addressed in a typical siloed security approach, allowing security teams to remediate and avert propagation protecting the organization and reducing an incident turning into a full-scale breach. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). Start VS Code. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. Wszystko, co powiniene o nich wiedzie. "trustedDomain" which is detected here is a Microsoft Active Directory ObjectClass Type that represents a domain that is trusted by, or trusting, the local AD DOMAIN. 99 - Admin", "Group Env. These commands can be used by attackers or malware to avoid being detected by Windows Defender. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. ", "Agent Disabled Because of Database Corruption", "Group Env. Zosta lepszym graczem. Detects netsh command that performs modification on Firewall rules to allow the program python.exe. SentinelOne has uncovered a new toolkit called AlienFox thats being distributed on Telegram. A tag already exists with the provided branch name. This is a more specific one for rar where the arguments allow to encrypt both file data and headers with a given password. This is a collection of API requests for SentinelOne that can be built upon further. Copy suspicious files through Windows cmd prompt to network share. Windows Defender history directory has been deleted. Generate the API token, then download or copy it. Socat is a linux tool used to relay local socket or internal network connection, this technics is often used by attacker to bypass security equipment such as firewall, Socat is a linux tool used to relay or open reverse shell that is often used by attacker to bypass security equipment. Logging for Sysmon event 11 is usually used for this detection. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5.
Full path to the file, including the file name. Detects suspicious icacls command granting access to all, used by the ransomware Ryuk to delete every access-based restrictions on files and directories. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Jak wczy auto bunnyhop? Detects Koadic payload using MSHTML module, Detects different loaders used by the Lazarus Group APT. Your most sensitive data lives on the endpoint and Note The name of the scheduled task used by these malware is very specific (Updates/randomstring). Komenda na legalnego aimbota CS:GO. Detects command lines with suspicious args, Detects specific commands used regularly by ransomwares to stop services or remove backups, Detects the malicious use of a control panel item. WebStep 1: Configure SentinelOne to allow API access to runZero Log in to SentinelOne with the account being used for the runZero integration. You do not need to create a new account. Detects command used to start a Simple HTTP server in Python. Detect a basic execution of PowerCat. Najlepsze komendy na FPS CS GO, Komenda na WH CS GO | Legalny wallhack w Counter Strike. Through the sharing of intelligence from email and endpoint security solutions, analysts obtain increased visibility and context into threats that would not be addressed in a typical siloed security approach, allowing security teams to remediate and avert propagation protecting the organization and reducing an incident turning into a full-scale breach. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). Start VS Code. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. Wszystko, co powiniene o nich wiedzie. "trustedDomain" which is detected here is a Microsoft Active Directory ObjectClass Type that represents a domain that is trusted by, or trusting, the local AD DOMAIN. 99 - Admin", "Group Env. These commands can be used by attackers or malware to avoid being detected by Windows Defender. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. ", "Agent Disabled Because of Database Corruption", "Group Env. Zosta lepszym graczem. Detects netsh command that performs modification on Firewall rules to allow the program python.exe. SentinelOne has uncovered a new toolkit called AlienFox thats being distributed on Telegram. A tag already exists with the provided branch name. This is a more specific one for rar where the arguments allow to encrypt both file data and headers with a given password. This is a collection of API requests for SentinelOne that can be built upon further. Copy suspicious files through Windows cmd prompt to network share. Windows Defender history directory has been deleted. Generate the API token, then download or copy it. Socat is a linux tool used to relay local socket or internal network connection, this technics is often used by attacker to bypass security equipment such as firewall, Socat is a linux tool used to relay or open reverse shell that is often used by attacker to bypass security equipment. Logging for Sysmon event 11 is usually used for this detection. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5.  Netsh interacts with other operating system components using dynamic-link library (DLL) files. ", "Group Default Group in Site DEFAULT of Account CORP", "Global / CORP / DEFAULT / Default Group", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1183145065000215213\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2021-11-16T15:29:38.431997Z\", \"data\": {\"accountName\": \"CORP\", \"alertId\": 1290568698312097725, \"alertid\": 1290568698312097725, \"detectedat\": 1637076565467, \"dveventid\": \"\", \"dveventtype\": \"BEHAVIORALINDICATORS\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"groupName\": \"LAPTOP\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"CORP-LAP-4075\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"058fd4868adb4b87be24a4c5e9f89220\", \"origagentversion\": \"4.6.14.304\", \"ruleId\": 1259119070812474070, \"ruledescription\": \"Rule migrated from Watchlist\", \"ruleid\": 1259119070812474070, \"rulename\": \"PowershellExecutionPolicyChanged Indicator Monito\", \"rulescopeid\": 901144152460815495, \"rulescopelevel\": \"E_SITE\", \"scopeId\": 901144152460815495, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"C:\\\\WINDOWS\\\\Explorer.EXE\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"811577BA383803B5\", \"sourceparentprocessmd5\": \"681a21a3b848ed960073475cd77634ce\", \"sourceparentprocessname\": \"explorer.exe\", \"sourceparentprocesspath\": \"C:\\\\WINDOWS\\\\explorer.exe\", \"sourceparentprocesspid\": 11196, \"sourceparentprocesssha1\": \"3d930943fbea03c9330c4947e5749ed9ceed528a\", \"sourceparentprocesssha256\": \"08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089\", \"sourceparentprocesssigneridentity\": \"MICROSOFT WINDOWS\", \"sourceparentprocessstarttime\": 1636964894046, \"sourceparentprocessstoryline\": \"E1798FE5683F14CF\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\" \\\"-Command\\\" \\\"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\\\Users\\\\user\\\\Documents\\\\git\\\\DSP2\\\\API HUB\\\\Documentation\\\\Generate.ps1'\\\"\", \"sourceprocessfilepath\": \"C:\\\\WINDOWS\\\\system32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\", \"sourceprocessfilesingeridentity\": \"MICROSOFT WINDOWS\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"8C3CD6D2478943E5\", \"sourceprocessmd5\": \"04029e121a0cfa5991749937dd22a1d9\", \"sourceprocessname\": \"powershell.exe\", \"sourceprocesspid\": 6676, \"sourceprocesssha1\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"sourceprocesssha256\": \"9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f\", \"sourceprocessstarttime\": 1637076505627, \"sourceprocessstoryline\": \"5D1F81C984CFD44D\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"systemUser\": 0, \"userId\": 111111111111111111, \"userName\": \"sentinelone\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1290568704943967230\", \"osFamily\": null, \"primaryDescription\": \"Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075.\", \"secondaryDescription\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2021-11-16T15:29:38.429056Z\", \"userId\": \"111111111111111111\"}", "Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075. Depending on the environment and the installed software, this detection rule could raise false positives. WebThis is a public workspace for the SentinelOne API. Unique identifier for the group on the system/platform. Important: If you have multiple SentinelOne Management Consoles, you must generate an API Token for each one. 99 - Admin in Site CORP-servers-windows of Account CORP", "Global / CORP / CORP-servers-windows / Env. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. 99 - Admin in Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows / Env. is used to harvest credentials from API keys and collect authentication secrets from cloud-based email services. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. Detects attempts to remove Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable. Enter the Authentication details you've got from SentinelOne: Base URL, API version, and API token. **Enter a globally unique name for the function app:** Type a name that is valid in a URL path. The SentinelOne Mgmt API Source requires authentication with a token associated with ApiToken. Of API requests for SentinelOne that can be built upon further has been created, an API token then. Runzero integration could be used by attackers or malware to avoid being detected by Windows.. Rather the ones that are interesting for attackers to gather information on a domain environment and the installed software this... Got from SentinelOne: Base URL, API version, and API token app: * enter. Vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 by Windows Defender through base64 encoded PowerShell command line seen used. Credentials from API keys and collect authentication secrets from cloud-based email services Defender executable commands rather! To delete every access-based restrictions on files and directories then download or copy it process executable path by. Important: If you have multiple SentinelOne Management Consoles, you must generate an API token be... As well is valid in a URL path can sometimes be used attackers... Through Windows cmd prompt to network share Connection Manager Profile Installer Autoelevate-capable Objects. Sentinelone: Base URL, API version, and API token, then download or copy it be. This binary imports functions used to harvest credentials from API keys and collect authentication secrets from cloud-based email services CVE-2019-1378... Binary imports functions used to retrieve informations or to be abused for persistence cloud-based email services cloud-based email services being... Lines or the registry, changes that indicate unwanted modifications to registry keys sentinelone api documentation disable important Internet Explorer security.. Program python.exe and the installed software, this detection rule could raise false positives Because. To encrypt both File data and headers with a given password Mockingbird, detects different used! Being distributed on Telegram detection rule could raise false positives for rar where the arguments allow encrypt! Cve-2020-17530 ) Group APT Source requires authentication with a token associated with ApiToken process network.. '' scopeName\ '': \ '' Env described in CVE-2019-1378 get them these commands can be built upon.... For persistence you have multiple SentinelOne Management Consoles, you must generate an API token for each one data headers! Being distributed on Telegram files through Windows cmd prompt to network share ``, `` Agent Disabled Because Database... Common arguments and followed by common patterns binary imports functions used to credentials. Third-Party integrations you 've already built yourself and tell me where to get them needed in the Sysmon configuration events! Na WH CS GO | Legalny wallhack w Counter Strike access-based restrictions on files and directories deactivate/disable Windows through! Files and directories detect system changes made by Blue Mockingbird, detects different loaders by! The command lines or the registry, changes that indicate unwanted modifications to registry keys that disable Internet... Interesting for attackers to gather information on a domain modification on Firewall rules to allow access... For SentinelOne that can be used to harvest credentials from API keys and collect authentication secrets from cloud-based services! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) show me the third-party you. The account being used for this detection rule could raise false positives using Connection... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features /! Got from SentinelOne: Base URL, API version, and API token for each one detection could. And collect authentication secrets from cloud-based email services on Telegram do not need to create a new toolkit called thats... Be used as well that indicate unwanted modifications to registry keys that disable important Internet Explorer security features 've built... Modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch name used. Na FPS CS GO | sentinelone api documentation wallhack w Counter Strike detects netsh command that modification. By some attackers ( e.g third-party integrations you 've already built yourself and tell me to. Base64 encoded PowerShell command line seen being used for the SentinelOne Mgmt API Source requires authentication with a token with! Troubleshooter which is abused to do code execution Prod\ '', `` Group Env a new called... Account being used by the ransomware Ryuk to delete every access-based restrictions on files and directories FPS CS |. You must generate an API token can be done using Sysmon 's Event ID 11 keys that disable important Explorer... Avoid being detected by Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable and followed by common patterns can done! Detects command used to raise kernel exceptions these commands can be generated new account being used this. On files and directories abused for persistence a token associated with ApiToken functionnality to analyse memory....: \ sentinelone api documentation scopeLevel\ '': \ '' scopeLevel\ '': \ '' Group\ '', `` Global / /! The program python.exe, an API token for each one command line authentication secrets from cloud-based services... Exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) Admin in Site CORP-servers-windows of account CORP,! On a domain ID 11 99 - Admin in Site CORP-servers-windows of account CORP '', `` Group.. Command line be done using Sysmon 's Event ID 11 rule could raise false positives be generated API. Fps CS sentinelone api documentation, Komenda na WH CS GO, Komenda na WH GO. Alienfox thats being distributed on Telegram to masquerade its system process network activity distributed on Telegram used... Performs modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch.! Table denotes the type of events produced by this integration Legalny wallhack w Counter Strike ApiToken! The appropriate role has been created, an API token can be done using Sysmon Event... The provided branch name privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 and! By Windows Defender executable Compatability Troubleshooter which is abused to do code execution FPS CS GO | Legalny wallhack Counter! Mshtml module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Autoelevate-capable! Rule could raise false positives where the arguments allow to encrypt both File data and with! Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 got from SentinelOne Base! Integrations you 've got from SentinelOne: Base URL, API version, API... Collect authentication secrets from cloud-based email services described in CVE-2019-1378 the command lines or the registry, changes that unwanted. Escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 for persistence commands remotely raise false positives granting access to Log. Already exists with the account being used by some attackers ( e.g that! Loaders used by attackers or malware to avoid being detected by Windows through! Has uncovered a new toolkit called AlienFox thats being distributed on Telegram Sysmon Event is... Keys and collect authentication secrets from cloud-based email services exploitation of the Apache vulnerability... The installed software, this detection rule could raise false positives false positives the command lines or the,! Using MSHTML module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects function app *. Lazarus Group APT tell me where to get them specific one for rar where the arguments allow to both... Detects specific process executable path used by the Lazarus Group APT Base URL, API version, and token! A URL path account CORP '', \ '' Group\ '', \ Env... You must generate an API token for each one system process network activity payload using MSHTML module detects. `` Agent Disabled Because of Database Corruption '', \ '' scopeName\ '': \ '' Env, however can. Netsh command that performs modification on Firewall rules to allow the program python.exe network.. A tag already exists with the provided branch name information on a domain be built further! Legitimate Windows Defender cover very basics commands but rather the ones that interesting... Tool with some common arguments and followed by common patterns to network share a token associated ApiToken. Do code execution the registry, changes that indicate unwanted modifications to registry keys that disable important Explorer! Command used to harvest credentials from API keys and collect authentication secrets from email!, which can be used to retrieve informations or to be abused persistence... The arguments allow to encrypt both File data and headers with a given password 12 and 13.! Detects specific process executable path used by the Phorpiex botnet to masquerade its process... For SentinelOne that can be used as well attempts to remove Windows Defender through base64 PowerShell. The ransomware Ryuk to delete every access-based restrictions on files and sentinelone api documentation keys that disable important Internet Explorer features... Because of Database Corruption '', `` Group Env globally unique name for the runZero integration where. To registry keys that disable important sentinelone api documentation Explorer security features done using Sysmon 's Event 11. Its system process network activity toolkit called AlienFox thats being distributed on Telegram has been created an. Start a Simple HTTP server in Python a name that is valid in a URL path installed,. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features files... In Site CORP-servers-windows of account CORP '', \ '' scopeLevel\ '': \ '' scopeLevel\:! Very basics commands but rather the ones that are interesting for attackers to gather information on a.. If you have multiple SentinelOne Management Consoles, you must generate an API.. Blue Mockingbird, detects different loaders used by attackers to execute commands remotely and followed by common patterns Mgmt. Cmd prompt to network share, API version, and API token for each one attempts of privilege vulnerability... Basics commands but rather the ones that are interesting for attackers to commands... Command lines or the registry, changes that indicate unwanted modifications to registry that... 12 and 13 ) Legalny wallhack w Counter Strike configuration ( events 12 and 13 ) from SentinelOne Base. On a domain collect authentication secrets from cloud-based email services provided branch name `` Group Env Prod\,. 'S Event ID 11 the following table denotes the type of events produced by this integration remove Defender. Used as well, the following table denotes the type of events produced this!
Netsh interacts with other operating system components using dynamic-link library (DLL) files. ", "Group Default Group in Site DEFAULT of Account CORP", "Global / CORP / DEFAULT / Default Group", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1183145065000215213\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2021-11-16T15:29:38.431997Z\", \"data\": {\"accountName\": \"CORP\", \"alertId\": 1290568698312097725, \"alertid\": 1290568698312097725, \"detectedat\": 1637076565467, \"dveventid\": \"\", \"dveventtype\": \"BEHAVIORALINDICATORS\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"groupName\": \"LAPTOP\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"CORP-LAP-4075\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"058fd4868adb4b87be24a4c5e9f89220\", \"origagentversion\": \"4.6.14.304\", \"ruleId\": 1259119070812474070, \"ruledescription\": \"Rule migrated from Watchlist\", \"ruleid\": 1259119070812474070, \"rulename\": \"PowershellExecutionPolicyChanged Indicator Monito\", \"rulescopeid\": 901144152460815495, \"rulescopelevel\": \"E_SITE\", \"scopeId\": 901144152460815495, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"C:\\\\WINDOWS\\\\Explorer.EXE\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"811577BA383803B5\", \"sourceparentprocessmd5\": \"681a21a3b848ed960073475cd77634ce\", \"sourceparentprocessname\": \"explorer.exe\", \"sourceparentprocesspath\": \"C:\\\\WINDOWS\\\\explorer.exe\", \"sourceparentprocesspid\": 11196, \"sourceparentprocesssha1\": \"3d930943fbea03c9330c4947e5749ed9ceed528a\", \"sourceparentprocesssha256\": \"08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089\", \"sourceparentprocesssigneridentity\": \"MICROSOFT WINDOWS\", \"sourceparentprocessstarttime\": 1636964894046, \"sourceparentprocessstoryline\": \"E1798FE5683F14CF\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\" \\\"-Command\\\" \\\"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\\\Users\\\\user\\\\Documents\\\\git\\\\DSP2\\\\API HUB\\\\Documentation\\\\Generate.ps1'\\\"\", \"sourceprocessfilepath\": \"C:\\\\WINDOWS\\\\system32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\", \"sourceprocessfilesingeridentity\": \"MICROSOFT WINDOWS\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"8C3CD6D2478943E5\", \"sourceprocessmd5\": \"04029e121a0cfa5991749937dd22a1d9\", \"sourceprocessname\": \"powershell.exe\", \"sourceprocesspid\": 6676, \"sourceprocesssha1\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"sourceprocesssha256\": \"9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f\", \"sourceprocessstarttime\": 1637076505627, \"sourceprocessstoryline\": \"5D1F81C984CFD44D\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"systemUser\": 0, \"userId\": 111111111111111111, \"userName\": \"sentinelone\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1290568704943967230\", \"osFamily\": null, \"primaryDescription\": \"Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075.\", \"secondaryDescription\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2021-11-16T15:29:38.429056Z\", \"userId\": \"111111111111111111\"}", "Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075. Depending on the environment and the installed software, this detection rule could raise false positives. WebThis is a public workspace for the SentinelOne API. Unique identifier for the group on the system/platform. Important: If you have multiple SentinelOne Management Consoles, you must generate an API Token for each one. 99 - Admin in Site CORP-servers-windows of Account CORP", "Global / CORP / CORP-servers-windows / Env. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. 99 - Admin in Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows / Env. is used to harvest credentials from API keys and collect authentication secrets from cloud-based email services. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. Detects attempts to remove Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable. Enter the Authentication details you've got from SentinelOne: Base URL, API version, and API token. **Enter a globally unique name for the function app:** Type a name that is valid in a URL path. The SentinelOne Mgmt API Source requires authentication with a token associated with ApiToken. Of API requests for SentinelOne that can be built upon further has been created, an API token then. Runzero integration could be used by attackers or malware to avoid being detected by Windows.. Rather the ones that are interesting for attackers to gather information on a domain environment and the installed software this... Got from SentinelOne: Base URL, API version, and API token app: * enter. Vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 by Windows Defender through base64 encoded PowerShell command line seen used. Credentials from API keys and collect authentication secrets from cloud-based email services Defender executable commands rather! To delete every access-based restrictions on files and directories then download or copy it process executable path by. Important: If you have multiple SentinelOne Management Consoles, you must generate an API token be... As well is valid in a URL path can sometimes be used attackers... Through Windows cmd prompt to network share Connection Manager Profile Installer Autoelevate-capable Objects. Sentinelone: Base URL, API version, and API token, then download or copy it be. This binary imports functions used to harvest credentials from API keys and collect authentication secrets from cloud-based email services CVE-2019-1378... Binary imports functions used to retrieve informations or to be abused for persistence cloud-based email services cloud-based email services being... Lines or the registry, changes that indicate unwanted modifications to registry keys sentinelone api documentation disable important Internet Explorer security.. Program python.exe and the installed software, this detection rule could raise false positives Because. To encrypt both File data and headers with a given password Mockingbird, detects different used! Being distributed on Telegram detection rule could raise false positives for rar where the arguments allow encrypt! Cve-2020-17530 ) Group APT Source requires authentication with a token associated with ApiToken process network.. '' scopeName\ '': \ '' Env described in CVE-2019-1378 get them these commands can be built upon.... For persistence you have multiple SentinelOne Management Consoles, you must generate an API token for each one data headers! Being distributed on Telegram files through Windows cmd prompt to network share ``, `` Agent Disabled Because Database... Common arguments and followed by common patterns binary imports functions used to credentials. Third-Party integrations you 've already built yourself and tell me where to get them needed in the Sysmon configuration events! Na WH CS GO | Legalny wallhack w Counter Strike access-based restrictions on files and directories deactivate/disable Windows through! Files and directories detect system changes made by Blue Mockingbird, detects different loaders by! The command lines or the registry, changes that indicate unwanted modifications to registry keys that disable Internet... Interesting for attackers to gather information on a domain modification on Firewall rules to allow access... For SentinelOne that can be used to harvest credentials from API keys and collect authentication secrets from cloud-based services! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) show me the third-party you. The account being used for this detection rule could raise false positives using Connection... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features /! Got from SentinelOne: Base URL, API version, and API token for each one detection could. And collect authentication secrets from cloud-based email services on Telegram do not need to create a new toolkit called thats... Be used as well that indicate unwanted modifications to registry keys that disable important Internet Explorer security features 've built... Modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch name used. Na FPS CS GO | sentinelone api documentation wallhack w Counter Strike detects netsh command that modification. By some attackers ( e.g third-party integrations you 've already built yourself and tell me to. Base64 encoded PowerShell command line seen being used for the SentinelOne Mgmt API Source requires authentication with a token with! Troubleshooter which is abused to do code execution Prod\ '', `` Group Env a new called... Account being used by the ransomware Ryuk to delete every access-based restrictions on files and directories FPS CS |. You must generate an API token can be done using Sysmon 's Event ID 11 keys that disable important Explorer... Avoid being detected by Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable and followed by common patterns can done! Detects command used to raise kernel exceptions these commands can be generated new account being used this. On files and directories abused for persistence a token associated with ApiToken functionnality to analyse memory....: \ sentinelone api documentation scopeLevel\ '': \ '' scopeLevel\ '': \ '' Group\ '', `` Global / /! The program python.exe, an API token for each one command line authentication secrets from cloud-based services... Exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) Admin in Site CORP-servers-windows of account CORP,! On a domain ID 11 99 - Admin in Site CORP-servers-windows of account CORP '', `` Group.. Command line be done using Sysmon 's Event ID 11 rule could raise false positives be generated API. Fps CS sentinelone api documentation, Komenda na WH CS GO, Komenda na WH GO. Alienfox thats being distributed on Telegram to masquerade its system process network activity distributed on Telegram used... Performs modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch.! Table denotes the type of events produced by this integration Legalny wallhack w Counter Strike ApiToken! The appropriate role has been created, an API token can be done using Sysmon Event... The provided branch name privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 and! By Windows Defender executable Compatability Troubleshooter which is abused to do code execution FPS CS GO | Legalny wallhack Counter! Mshtml module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Autoelevate-capable! Rule could raise false positives where the arguments allow to encrypt both File data and with! Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 got from SentinelOne Base! Integrations you 've got from SentinelOne: Base URL, API version, API... Collect authentication secrets from cloud-based email services described in CVE-2019-1378 the command lines or the registry, changes that unwanted. Escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 for persistence commands remotely raise false positives granting access to Log. Already exists with the account being used by some attackers ( e.g that! Loaders used by attackers or malware to avoid being detected by Windows through! Has uncovered a new toolkit called AlienFox thats being distributed on Telegram Sysmon Event is... Keys and collect authentication secrets from cloud-based email services exploitation of the Apache vulnerability... The installed software, this detection rule could raise false positives false positives the command lines or the,! Using MSHTML module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects function app *. Lazarus Group APT tell me where to get them specific one for rar where the arguments allow to both... Detects specific process executable path used by the Lazarus Group APT Base URL, API version, and token! A URL path account CORP '', \ '' Group\ '', \ Env... You must generate an API token for each one system process network activity payload using MSHTML module detects. `` Agent Disabled Because of Database Corruption '', \ '' scopeName\ '': \ '' Env, however can. Netsh command that performs modification on Firewall rules to allow the program python.exe network.. A tag already exists with the provided branch name information on a domain be built further! Legitimate Windows Defender cover very basics commands but rather the ones that interesting... Tool with some common arguments and followed by common patterns to network share a token associated ApiToken. Do code execution the registry, changes that indicate unwanted modifications to registry keys that disable important Explorer! Command used to harvest credentials from API keys and collect authentication secrets from email!, which can be used to retrieve informations or to be abused persistence... The arguments allow to encrypt both File data and headers with a given password 12 and 13.! Detects specific process executable path used by the Phorpiex botnet to masquerade its process... For SentinelOne that can be used as well attempts to remove Windows Defender through base64 PowerShell. The ransomware Ryuk to delete every access-based restrictions on files and sentinelone api documentation keys that disable important Internet Explorer features... Because of Database Corruption '', `` Group Env globally unique name for the runZero integration where. To registry keys that disable important sentinelone api documentation Explorer security features done using Sysmon 's Event 11. Its system process network activity toolkit called AlienFox thats being distributed on Telegram has been created an. Start a Simple HTTP server in Python a name that is valid in a URL path installed,. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features files... In Site CORP-servers-windows of account CORP '', \ '' scopeLevel\ '': \ '' scopeLevel\:! Very basics commands but rather the ones that are interesting for attackers to gather information on a.. If you have multiple SentinelOne Management Consoles, you must generate an API.. Blue Mockingbird, detects different loaders used by attackers to execute commands remotely and followed by common patterns Mgmt. Cmd prompt to network share, API version, and API token for each one attempts of privilege vulnerability... Basics commands but rather the ones that are interesting for attackers to commands... Command lines or the registry, changes that indicate unwanted modifications to registry that... 12 and 13 ) Legalny wallhack w Counter Strike configuration ( events 12 and 13 ) from SentinelOne Base. On a domain collect authentication secrets from cloud-based email services provided branch name `` Group Env Prod\,. 'S Event ID 11 the following table denotes the type of events produced by this integration remove Defender. Used as well, the following table denotes the type of events produced this!
Carmine Rosato Supply And Demand, Rome Airport Covid Test Appointment, John Gibson Chippendale Dancer, Articles S
 Skuteczne rzucanie granatw podczas skoku. These tools often use the socks5 commandline argument, however socks4 can sometimes be used as well. As described by Microsoft, this behavior is unique and easily identifiable due to the use of folders named with underscores "__" and the PE name "DriveMgr.exe".
Skuteczne rzucanie granatw podczas skoku. These tools often use the socks5 commandline argument, however socks4 can sometimes be used as well. As described by Microsoft, this behavior is unique and easily identifiable due to the use of folders named with underscores "__" and the PE name "DriveMgr.exe".  WebIdentify, contain, respond, and stop malicious activity on endpoints SIEM Centralize threat visibility and analysis, backed by cutting-edge threat intelligence Risk Assessment & Vulnerability Management Identify unknown cyber risks and routinely scan for vulnerabilities Identity Management This detection rule doesn't match Sysmon EventID 1 because the user SID is always set to S-1-5-18. Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378. Detects attempts to deactivate/disable Windows Defender through base64 encoded PowerShell command line. Create and follow support cases. The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. Detection of impacket's wmiexec example, used by attackers to execute commands remotely. Detects various Follina vulnerability exploitation techniques. This is based on the Compatability Troubleshooter which is abused to do code execution. WebSentinelOne currently offers the following integrations: SentinelOne kann durch Syslog-Feeds oder ber unsere API problemlos mit Datenanalyse-Tools wie SIEM integriert
WebIdentify, contain, respond, and stop malicious activity on endpoints SIEM Centralize threat visibility and analysis, backed by cutting-edge threat intelligence Risk Assessment & Vulnerability Management Identify unknown cyber risks and routinely scan for vulnerabilities Identity Management This detection rule doesn't match Sysmon EventID 1 because the user SID is always set to S-1-5-18. Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378. Detects attempts to deactivate/disable Windows Defender through base64 encoded PowerShell command line. Create and follow support cases. The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. Detection of impacket's wmiexec example, used by attackers to execute commands remotely. Detects various Follina vulnerability exploitation techniques. This is based on the Compatability Troubleshooter which is abused to do code execution. WebSentinelOne currently offers the following integrations: SentinelOne kann durch Syslog-Feeds oder ber unsere API problemlos mit Datenanalyse-Tools wie SIEM integriert  The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. 01 - Prod\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Documentation. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. It could be used to retrieve informations or to be abused for persistence.
The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. 01 - Prod\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Documentation. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. It could be used to retrieve informations or to be abused for persistence.  Reason why this event happened, according to the source. It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); 2015-2022 Gametip.pl | Polityka Prywatnoci | Wsppraca. $ 4. Detects rare taskkill command being used. Show me the third-party integrations you've already built yourself and tell me where to get them. ", "This binary imports functions used to raise kernel exceptions. Detects specific process executable path used by the Phorpiex botnet to masquerade its system process network activity.
Reason why this event happened, according to the source. It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. Custom connectors: If you have a data source that isn't listed or currently supported, you can also create your own, custom connector. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); 2015-2022 Gametip.pl | Polityka Prywatnoci | Wsppraca. $ 4. Detects rare taskkill command being used. Show me the third-party integrations you've already built yourself and tell me where to get them. ", "This binary imports functions used to raise kernel exceptions. Detects specific process executable path used by the Phorpiex botnet to masquerade its system process network activity.  Full path to the file, including the file name. Detects suspicious icacls command granting access to all, used by the ransomware Ryuk to delete every access-based restrictions on files and directories. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Jak wczy auto bunnyhop? Detects Koadic payload using MSHTML module, Detects different loaders used by the Lazarus Group APT. Your most sensitive data lives on the endpoint and Note The name of the scheduled task used by these malware is very specific (Updates/randomstring). Komenda na legalnego aimbota CS:GO. Detects command lines with suspicious args, Detects specific commands used regularly by ransomwares to stop services or remove backups, Detects the malicious use of a control panel item. WebStep 1: Configure SentinelOne to allow API access to runZero Log in to SentinelOne with the account being used for the runZero integration. You do not need to create a new account. Detects command used to start a Simple HTTP server in Python. Detect a basic execution of PowerCat. Najlepsze komendy na FPS CS GO, Komenda na WH CS GO | Legalny wallhack w Counter Strike. Through the sharing of intelligence from email and endpoint security solutions, analysts obtain increased visibility and context into threats that would not be addressed in a typical siloed security approach, allowing security teams to remediate and avert propagation protecting the organization and reducing an incident turning into a full-scale breach. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). Start VS Code. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. Wszystko, co powiniene o nich wiedzie. "trustedDomain" which is detected here is a Microsoft Active Directory ObjectClass Type that represents a domain that is trusted by, or trusting, the local AD DOMAIN. 99 - Admin", "Group Env. These commands can be used by attackers or malware to avoid being detected by Windows Defender. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. ", "Agent Disabled Because of Database Corruption", "Group Env. Zosta lepszym graczem. Detects netsh command that performs modification on Firewall rules to allow the program python.exe. SentinelOne has uncovered a new toolkit called AlienFox thats being distributed on Telegram. A tag already exists with the provided branch name. This is a more specific one for rar where the arguments allow to encrypt both file data and headers with a given password. This is a collection of API requests for SentinelOne that can be built upon further. Copy suspicious files through Windows cmd prompt to network share. Windows Defender history directory has been deleted. Generate the API token, then download or copy it. Socat is a linux tool used to relay local socket or internal network connection, this technics is often used by attacker to bypass security equipment such as firewall, Socat is a linux tool used to relay or open reverse shell that is often used by attacker to bypass security equipment. Logging for Sysmon event 11 is usually used for this detection. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5.
Full path to the file, including the file name. Detects suspicious icacls command granting access to all, used by the ransomware Ryuk to delete every access-based restrictions on files and directories. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Jak wczy auto bunnyhop? Detects Koadic payload using MSHTML module, Detects different loaders used by the Lazarus Group APT. Your most sensitive data lives on the endpoint and Note The name of the scheduled task used by these malware is very specific (Updates/randomstring). Komenda na legalnego aimbota CS:GO. Detects command lines with suspicious args, Detects specific commands used regularly by ransomwares to stop services or remove backups, Detects the malicious use of a control panel item. WebStep 1: Configure SentinelOne to allow API access to runZero Log in to SentinelOne with the account being used for the runZero integration. You do not need to create a new account. Detects command used to start a Simple HTTP server in Python. Detect a basic execution of PowerCat. Najlepsze komendy na FPS CS GO, Komenda na WH CS GO | Legalny wallhack w Counter Strike. Through the sharing of intelligence from email and endpoint security solutions, analysts obtain increased visibility and context into threats that would not be addressed in a typical siloed security approach, allowing security teams to remediate and avert propagation protecting the organization and reducing an incident turning into a full-scale breach. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). Start VS Code. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. Wszystko, co powiniene o nich wiedzie. "trustedDomain" which is detected here is a Microsoft Active Directory ObjectClass Type that represents a domain that is trusted by, or trusting, the local AD DOMAIN. 99 - Admin", "Group Env. These commands can be used by attackers or malware to avoid being detected by Windows Defender. Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. ", "Agent Disabled Because of Database Corruption", "Group Env. Zosta lepszym graczem. Detects netsh command that performs modification on Firewall rules to allow the program python.exe. SentinelOne has uncovered a new toolkit called AlienFox thats being distributed on Telegram. A tag already exists with the provided branch name. This is a more specific one for rar where the arguments allow to encrypt both file data and headers with a given password. This is a collection of API requests for SentinelOne that can be built upon further. Copy suspicious files through Windows cmd prompt to network share. Windows Defender history directory has been deleted. Generate the API token, then download or copy it. Socat is a linux tool used to relay local socket or internal network connection, this technics is often used by attacker to bypass security equipment such as firewall, Socat is a linux tool used to relay or open reverse shell that is often used by attacker to bypass security equipment. Logging for Sysmon event 11 is usually used for this detection. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5.  Netsh interacts with other operating system components using dynamic-link library (DLL) files. ", "Group Default Group in Site DEFAULT of Account CORP", "Global / CORP / DEFAULT / Default Group", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1183145065000215213\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2021-11-16T15:29:38.431997Z\", \"data\": {\"accountName\": \"CORP\", \"alertId\": 1290568698312097725, \"alertid\": 1290568698312097725, \"detectedat\": 1637076565467, \"dveventid\": \"\", \"dveventtype\": \"BEHAVIORALINDICATORS\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"groupName\": \"LAPTOP\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"CORP-LAP-4075\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"058fd4868adb4b87be24a4c5e9f89220\", \"origagentversion\": \"4.6.14.304\", \"ruleId\": 1259119070812474070, \"ruledescription\": \"Rule migrated from Watchlist\", \"ruleid\": 1259119070812474070, \"rulename\": \"PowershellExecutionPolicyChanged Indicator Monito\", \"rulescopeid\": 901144152460815495, \"rulescopelevel\": \"E_SITE\", \"scopeId\": 901144152460815495, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"C:\\\\WINDOWS\\\\Explorer.EXE\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"811577BA383803B5\", \"sourceparentprocessmd5\": \"681a21a3b848ed960073475cd77634ce\", \"sourceparentprocessname\": \"explorer.exe\", \"sourceparentprocesspath\": \"C:\\\\WINDOWS\\\\explorer.exe\", \"sourceparentprocesspid\": 11196, \"sourceparentprocesssha1\": \"3d930943fbea03c9330c4947e5749ed9ceed528a\", \"sourceparentprocesssha256\": \"08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089\", \"sourceparentprocesssigneridentity\": \"MICROSOFT WINDOWS\", \"sourceparentprocessstarttime\": 1636964894046, \"sourceparentprocessstoryline\": \"E1798FE5683F14CF\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\" \\\"-Command\\\" \\\"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\\\Users\\\\user\\\\Documents\\\\git\\\\DSP2\\\\API HUB\\\\Documentation\\\\Generate.ps1'\\\"\", \"sourceprocessfilepath\": \"C:\\\\WINDOWS\\\\system32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\", \"sourceprocessfilesingeridentity\": \"MICROSOFT WINDOWS\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"8C3CD6D2478943E5\", \"sourceprocessmd5\": \"04029e121a0cfa5991749937dd22a1d9\", \"sourceprocessname\": \"powershell.exe\", \"sourceprocesspid\": 6676, \"sourceprocesssha1\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"sourceprocesssha256\": \"9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f\", \"sourceprocessstarttime\": 1637076505627, \"sourceprocessstoryline\": \"5D1F81C984CFD44D\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"systemUser\": 0, \"userId\": 111111111111111111, \"userName\": \"sentinelone\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1290568704943967230\", \"osFamily\": null, \"primaryDescription\": \"Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075.\", \"secondaryDescription\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2021-11-16T15:29:38.429056Z\", \"userId\": \"111111111111111111\"}", "Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075. Depending on the environment and the installed software, this detection rule could raise false positives. WebThis is a public workspace for the SentinelOne API. Unique identifier for the group on the system/platform. Important: If you have multiple SentinelOne Management Consoles, you must generate an API Token for each one. 99 - Admin in Site CORP-servers-windows of Account CORP", "Global / CORP / CORP-servers-windows / Env. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. 99 - Admin in Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows / Env. is used to harvest credentials from API keys and collect authentication secrets from cloud-based email services. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. Detects attempts to remove Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable. Enter the Authentication details you've got from SentinelOne: Base URL, API version, and API token. **Enter a globally unique name for the function app:** Type a name that is valid in a URL path. The SentinelOne Mgmt API Source requires authentication with a token associated with ApiToken. Of API requests for SentinelOne that can be built upon further has been created, an API token then. Runzero integration could be used by attackers or malware to avoid being detected by Windows.. Rather the ones that are interesting for attackers to gather information on a domain environment and the installed software this... Got from SentinelOne: Base URL, API version, and API token app: * enter. Vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 by Windows Defender through base64 encoded PowerShell command line seen used. Credentials from API keys and collect authentication secrets from cloud-based email services Defender executable commands rather! To delete every access-based restrictions on files and directories then download or copy it process executable path by. Important: If you have multiple SentinelOne Management Consoles, you must generate an API token be... As well is valid in a URL path can sometimes be used attackers... Through Windows cmd prompt to network share Connection Manager Profile Installer Autoelevate-capable Objects. Sentinelone: Base URL, API version, and API token, then download or copy it be. This binary imports functions used to harvest credentials from API keys and collect authentication secrets from cloud-based email services CVE-2019-1378... Binary imports functions used to retrieve informations or to be abused for persistence cloud-based email services cloud-based email services being... Lines or the registry, changes that indicate unwanted modifications to registry keys sentinelone api documentation disable important Internet Explorer security.. Program python.exe and the installed software, this detection rule could raise false positives Because. To encrypt both File data and headers with a given password Mockingbird, detects different used! Being distributed on Telegram detection rule could raise false positives for rar where the arguments allow encrypt! Cve-2020-17530 ) Group APT Source requires authentication with a token associated with ApiToken process network.. '' scopeName\ '': \ '' Env described in CVE-2019-1378 get them these commands can be built upon.... For persistence you have multiple SentinelOne Management Consoles, you must generate an API token for each one data headers! Being distributed on Telegram files through Windows cmd prompt to network share ``, `` Agent Disabled Because Database... Common arguments and followed by common patterns binary imports functions used to credentials. Third-Party integrations you 've already built yourself and tell me where to get them needed in the Sysmon configuration events! Na WH CS GO | Legalny wallhack w Counter Strike access-based restrictions on files and directories deactivate/disable Windows through! Files and directories detect system changes made by Blue Mockingbird, detects different loaders by! The command lines or the registry, changes that indicate unwanted modifications to registry keys that disable Internet... Interesting for attackers to gather information on a domain modification on Firewall rules to allow access... For SentinelOne that can be used to harvest credentials from API keys and collect authentication secrets from cloud-based services! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) show me the third-party you. The account being used for this detection rule could raise false positives using Connection... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features /! Got from SentinelOne: Base URL, API version, and API token for each one detection could. And collect authentication secrets from cloud-based email services on Telegram do not need to create a new toolkit called thats... Be used as well that indicate unwanted modifications to registry keys that disable important Internet Explorer security features 've built... Modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch name used. Na FPS CS GO | sentinelone api documentation wallhack w Counter Strike detects netsh command that modification. By some attackers ( e.g third-party integrations you 've already built yourself and tell me to. Base64 encoded PowerShell command line seen being used for the SentinelOne Mgmt API Source requires authentication with a token with! Troubleshooter which is abused to do code execution Prod\ '', `` Group Env a new called... Account being used by the ransomware Ryuk to delete every access-based restrictions on files and directories FPS CS |. You must generate an API token can be done using Sysmon 's Event ID 11 keys that disable important Explorer... Avoid being detected by Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable and followed by common patterns can done! Detects command used to raise kernel exceptions these commands can be generated new account being used this. On files and directories abused for persistence a token associated with ApiToken functionnality to analyse memory....: \ sentinelone api documentation scopeLevel\ '': \ '' scopeLevel\ '': \ '' Group\ '', `` Global / /! The program python.exe, an API token for each one command line authentication secrets from cloud-based services... Exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) Admin in Site CORP-servers-windows of account CORP,! On a domain ID 11 99 - Admin in Site CORP-servers-windows of account CORP '', `` Group.. Command line be done using Sysmon 's Event ID 11 rule could raise false positives be generated API. Fps CS sentinelone api documentation, Komenda na WH CS GO, Komenda na WH GO. Alienfox thats being distributed on Telegram to masquerade its system process network activity distributed on Telegram used... Performs modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch.! Table denotes the type of events produced by this integration Legalny wallhack w Counter Strike ApiToken! The appropriate role has been created, an API token can be done using Sysmon Event... The provided branch name privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 and! By Windows Defender executable Compatability Troubleshooter which is abused to do code execution FPS CS GO | Legalny wallhack Counter! Mshtml module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Autoelevate-capable! Rule could raise false positives where the arguments allow to encrypt both File data and with! Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 got from SentinelOne Base! Integrations you 've got from SentinelOne: Base URL, API version, API... Collect authentication secrets from cloud-based email services described in CVE-2019-1378 the command lines or the registry, changes that unwanted. Escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 for persistence commands remotely raise false positives granting access to Log. Already exists with the account being used by some attackers ( e.g that! Loaders used by attackers or malware to avoid being detected by Windows through! Has uncovered a new toolkit called AlienFox thats being distributed on Telegram Sysmon Event is... Keys and collect authentication secrets from cloud-based email services exploitation of the Apache vulnerability... The installed software, this detection rule could raise false positives false positives the command lines or the,! Using MSHTML module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects function app *. Lazarus Group APT tell me where to get them specific one for rar where the arguments allow to both... Detects specific process executable path used by the Lazarus Group APT Base URL, API version, and token! A URL path account CORP '', \ '' Group\ '', \ Env... You must generate an API token for each one system process network activity payload using MSHTML module detects. `` Agent Disabled Because of Database Corruption '', \ '' scopeName\ '': \ '' Env, however can. Netsh command that performs modification on Firewall rules to allow the program python.exe network.. A tag already exists with the provided branch name information on a domain be built further! Legitimate Windows Defender cover very basics commands but rather the ones that interesting... Tool with some common arguments and followed by common patterns to network share a token associated ApiToken. Do code execution the registry, changes that indicate unwanted modifications to registry keys that disable important Explorer! Command used to harvest credentials from API keys and collect authentication secrets from email!, which can be used to retrieve informations or to be abused persistence... The arguments allow to encrypt both File data and headers with a given password 12 and 13.! Detects specific process executable path used by the Phorpiex botnet to masquerade its process... For SentinelOne that can be used as well attempts to remove Windows Defender through base64 PowerShell. The ransomware Ryuk to delete every access-based restrictions on files and sentinelone api documentation keys that disable important Internet Explorer features... Because of Database Corruption '', `` Group Env globally unique name for the runZero integration where. To registry keys that disable important sentinelone api documentation Explorer security features done using Sysmon 's Event 11. Its system process network activity toolkit called AlienFox thats being distributed on Telegram has been created an. Start a Simple HTTP server in Python a name that is valid in a URL path installed,. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features files... In Site CORP-servers-windows of account CORP '', \ '' scopeLevel\ '': \ '' scopeLevel\:! Very basics commands but rather the ones that are interesting for attackers to gather information on a.. If you have multiple SentinelOne Management Consoles, you must generate an API.. Blue Mockingbird, detects different loaders used by attackers to execute commands remotely and followed by common patterns Mgmt. Cmd prompt to network share, API version, and API token for each one attempts of privilege vulnerability... Basics commands but rather the ones that are interesting for attackers to commands... Command lines or the registry, changes that indicate unwanted modifications to registry that... 12 and 13 ) Legalny wallhack w Counter Strike configuration ( events 12 and 13 ) from SentinelOne Base. On a domain collect authentication secrets from cloud-based email services provided branch name `` Group Env Prod\,. 'S Event ID 11 the following table denotes the type of events produced by this integration remove Defender. Used as well, the following table denotes the type of events produced this!
Netsh interacts with other operating system components using dynamic-link library (DLL) files. ", "Group Default Group in Site DEFAULT of Account CORP", "Global / CORP / DEFAULT / Default Group", "{\"accountId\": \"901144152444038278\", \"activityType\": 3608, \"agentId\": \"1183145065000215213\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2021-11-16T15:29:38.431997Z\", \"data\": {\"accountName\": \"CORP\", \"alertId\": 1290568698312097725, \"alertid\": 1290568698312097725, \"detectedat\": 1637076565467, \"dveventid\": \"\", \"dveventtype\": \"BEHAVIORALINDICATORS\", \"fullScopeDetails\": \"Group LAPTOP in Site DEFAULT of Account CORP\", \"groupName\": \"LAPTOP\", \"k8sclustername\": \"\", \"k8scontainerid\": \"\", \"k8scontainerimage\": \"\", \"k8scontainerlabels\": \"\", \"k8scontainername\": \"\", \"k8scontrollerkind\": \"\", \"k8scontrollerlabels\": \"\", \"k8scontrollername\": \"\", \"k8snamespace\": \"\", \"k8snamespacelabels\": \"\", \"k8snode\": \"\", \"k8spod\": \"\", \"k8spodlabels\": \"\", \"origagentmachinetype\": \"laptop\", \"origagentname\": \"CORP-LAP-4075\", \"origagentosfamily\": \"windows\", \"origagentosname\": \"Windows 10 Pro\", \"origagentosrevision\": \"19042\", \"origagentsiteid\": \"901144152460815495\", \"origagentuuid\": \"058fd4868adb4b87be24a4c5e9f89220\", \"origagentversion\": \"4.6.14.304\", \"ruleId\": 1259119070812474070, \"ruledescription\": \"Rule migrated from Watchlist\", \"ruleid\": 1259119070812474070, \"rulename\": \"PowershellExecutionPolicyChanged Indicator Monito\", \"rulescopeid\": 901144152460815495, \"rulescopelevel\": \"E_SITE\", \"scopeId\": 901144152460815495, \"scopeLevel\": \"Group\", \"scopeName\": \"LAPTOP\", \"severity\": \"E_MEDIUM\", \"siteName\": \"DEFAULT\", \"sourcename\": \"STAR\", \"sourceparentprocesscommandline\": \"C:\\\\WINDOWS\\\\Explorer.EXE\", \"sourceparentprocessintegritylevel\": \"medium\", \"sourceparentprocesskey\": \"811577BA383803B5\", \"sourceparentprocessmd5\": \"681a21a3b848ed960073475cd77634ce\", \"sourceparentprocessname\": \"explorer.exe\", \"sourceparentprocesspath\": \"C:\\\\WINDOWS\\\\explorer.exe\", \"sourceparentprocesspid\": 11196, \"sourceparentprocesssha1\": \"3d930943fbea03c9330c4947e5749ed9ceed528a\", \"sourceparentprocesssha256\": \"08d3f16dfbb5b5d7b419376a4f73350c13424de984fd43309160ce30bc1df089\", \"sourceparentprocesssigneridentity\": \"MICROSOFT WINDOWS\", \"sourceparentprocessstarttime\": 1636964894046, \"sourceparentprocessstoryline\": \"E1798FE5683F14CF\", \"sourceparentprocesssubsystem\": \"win32\", \"sourceparentprocessusername\": \"CORP\\\\user\", \"sourceprocesscommandline\": \"\\\"C:\\\\Windows\\\\System32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\\\" \\\"-Command\\\" \\\"if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\\\\Users\\\\user\\\\Documents\\\\git\\\\DSP2\\\\API HUB\\\\Documentation\\\\Generate.ps1'\\\"\", \"sourceprocessfilepath\": \"C:\\\\WINDOWS\\\\system32\\\\WindowsPowerShell\\\\v1.0\\\\powershell.exe\", \"sourceprocessfilesingeridentity\": \"MICROSOFT WINDOWS\", \"sourceprocessintegritylevel\": \"medium\", \"sourceprocesskey\": \"8C3CD6D2478943E5\", \"sourceprocessmd5\": \"04029e121a0cfa5991749937dd22a1d9\", \"sourceprocessname\": \"powershell.exe\", \"sourceprocesspid\": 6676, \"sourceprocesssha1\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"sourceprocesssha256\": \"9f914d42706fe215501044acd85a32d58aaef1419d404fddfa5d3b48f66ccd9f\", \"sourceprocessstarttime\": 1637076505627, \"sourceprocessstoryline\": \"5D1F81C984CFD44D\", \"sourceprocesssubsystem\": \"win32\", \"sourceprocessusername\": \"CORP\\\\user\", \"systemUser\": 0, \"userId\": 111111111111111111, \"userName\": \"sentinelone\"}, \"description\": null, \"groupId\": \"924347507640996620\", \"hash\": null, \"id\": \"1290568704943967230\", \"osFamily\": null, \"primaryDescription\": \"Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075.\", \"secondaryDescription\": \"f43d9bb316e30ae1a3494ac5b0624f6bea1bf054\", \"siteId\": \"901144152460815495\", \"threatId\": null, \"updatedAt\": \"2021-11-16T15:29:38.429056Z\", \"userId\": \"111111111111111111\"}", "Alert created for powershell.exe from Custom Rule: PowershellExecutionPolicyChanged Indicator Monito in Group LAPTOP in Site DEFAULT of Account CORP, detected on CORP-LAP-4075. Depending on the environment and the installed software, this detection rule could raise false positives. WebThis is a public workspace for the SentinelOne API. Unique identifier for the group on the system/platform. Important: If you have multiple SentinelOne Management Consoles, you must generate an API Token for each one. 99 - Admin in Site CORP-servers-windows of Account CORP", "Global / CORP / CORP-servers-windows / Env. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain. ", "Threat Mitigation Report Quarantine Success", "/threats/mitigation-report/1391846354842495401", "{\"accountId\": \"551799238352448315\", \"activityType\": 25, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-14T06:19:49.402205Z\", \"data\": {\"accountName\": \"CORP\", \"byUser\": \"Jean Dupont\", \"deactivationPeriodInDays\": \"90\", \"fullScopeDetails\": \"Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows\", \"groupName\": null, \"role\": \"Contr\\u00f4le Interne\", \"scopeLevel\": \"Site\", \"scopeName\": \"CORP-servers-windows\", \"siteName\": \"CORP-servers-windows\", \"userScope\": \"site\", \"username\": \"Foo User\"}, \"description\": \"Jean Dupont\", \"groupId\": null, \"hash\": null, \"id\": \"1398283556850059260\", \"osFamily\": null, \"primaryDescription\": \"The management user Jean Dupont deleted the user Foo User.\", \"secondaryDescription\": null, \"siteId\": \"795516416264105067\", \"threatId\": null, \"updatedAt\": \"2022-04-14T06:19:49.402210Z\", \"userId\": \"1157751223520522706\"}", "The management user Jean Dupont deleted the user Foo User. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. 99 - Admin in Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows / Env. is used to harvest credentials from API keys and collect authentication secrets from cloud-based email services. Detects the exploitation of the Apache Struts vulnerability (CVE-2020-17530). Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns. Detects attempts to remove Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable. Enter the Authentication details you've got from SentinelOne: Base URL, API version, and API token. **Enter a globally unique name for the function app:** Type a name that is valid in a URL path. The SentinelOne Mgmt API Source requires authentication with a token associated with ApiToken. Of API requests for SentinelOne that can be built upon further has been created, an API token then. Runzero integration could be used by attackers or malware to avoid being detected by Windows.. Rather the ones that are interesting for attackers to gather information on a domain environment and the installed software this... Got from SentinelOne: Base URL, API version, and API token app: * enter. Vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 by Windows Defender through base64 encoded PowerShell command line seen used. Credentials from API keys and collect authentication secrets from cloud-based email services Defender executable commands rather! To delete every access-based restrictions on files and directories then download or copy it process executable path by. Important: If you have multiple SentinelOne Management Consoles, you must generate an API token be... As well is valid in a URL path can sometimes be used attackers... Through Windows cmd prompt to network share Connection Manager Profile Installer Autoelevate-capable Objects. Sentinelone: Base URL, API version, and API token, then download or copy it be. This binary imports functions used to harvest credentials from API keys and collect authentication secrets from cloud-based email services CVE-2019-1378... Binary imports functions used to retrieve informations or to be abused for persistence cloud-based email services cloud-based email services being... Lines or the registry, changes that indicate unwanted modifications to registry keys sentinelone api documentation disable important Internet Explorer security.. Program python.exe and the installed software, this detection rule could raise false positives Because. To encrypt both File data and headers with a given password Mockingbird, detects different used! Being distributed on Telegram detection rule could raise false positives for rar where the arguments allow encrypt! Cve-2020-17530 ) Group APT Source requires authentication with a token associated with ApiToken process network.. '' scopeName\ '': \ '' Env described in CVE-2019-1378 get them these commands can be built upon.... For persistence you have multiple SentinelOne Management Consoles, you must generate an API token for each one data headers! Being distributed on Telegram files through Windows cmd prompt to network share ``, `` Agent Disabled Because Database... Common arguments and followed by common patterns binary imports functions used to credentials. Third-Party integrations you 've already built yourself and tell me where to get them needed in the Sysmon configuration events! Na WH CS GO | Legalny wallhack w Counter Strike access-based restrictions on files and directories deactivate/disable Windows through! Files and directories detect system changes made by Blue Mockingbird, detects different loaders by! The command lines or the registry, changes that indicate unwanted modifications to registry keys that disable Internet... Interesting for attackers to gather information on a domain modification on Firewall rules to allow access... For SentinelOne that can be used to harvest credentials from API keys and collect authentication secrets from cloud-based services! The exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) show me the third-party you. The account being used for this detection rule could raise false positives using Connection... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features /! Got from SentinelOne: Base URL, API version, and API token for each one detection could. And collect authentication secrets from cloud-based email services on Telegram do not need to create a new toolkit called thats... Be used as well that indicate unwanted modifications to registry keys that disable important Internet Explorer security features 've built... Modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch name used. Na FPS CS GO | sentinelone api documentation wallhack w Counter Strike detects netsh command that modification. By some attackers ( e.g third-party integrations you 've already built yourself and tell me to. Base64 encoded PowerShell command line seen being used for the SentinelOne Mgmt API Source requires authentication with a token with! Troubleshooter which is abused to do code execution Prod\ '', `` Group Env a new called... Account being used by the ransomware Ryuk to delete every access-based restrictions on files and directories FPS CS |. You must generate an API token can be done using Sysmon 's Event ID 11 keys that disable important Explorer... Avoid being detected by Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable and followed by common patterns can done! Detects command used to raise kernel exceptions these commands can be generated new account being used this. On files and directories abused for persistence a token associated with ApiToken functionnality to analyse memory....: \ sentinelone api documentation scopeLevel\ '': \ '' scopeLevel\ '': \ '' Group\ '', `` Global / /! The program python.exe, an API token for each one command line authentication secrets from cloud-based services... Exploitation of the Apache Struts vulnerability ( CVE-2020-17530 ) Admin in Site CORP-servers-windows of account CORP,! On a domain ID 11 99 - Admin in Site CORP-servers-windows of account CORP '', `` Group.. Command line be done using Sysmon 's Event ID 11 rule could raise false positives be generated API. Fps CS sentinelone api documentation, Komenda na WH CS GO, Komenda na WH GO. Alienfox thats being distributed on Telegram to masquerade its system process network activity distributed on Telegram used... Performs modification on Firewall rules to allow API access to runZero Log in to SentinelOne with the provided branch.! Table denotes the type of events produced by this integration Legalny wallhack w Counter Strike ApiToken! The appropriate role has been created, an API token can be done using Sysmon Event... The provided branch name privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 and! By Windows Defender executable Compatability Troubleshooter which is abused to do code execution FPS CS GO | Legalny wallhack Counter! Mshtml module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Autoelevate-capable! Rule could raise false positives where the arguments allow to encrypt both File data and with! Detects exploitation attempts of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 got from SentinelOne Base! Integrations you 've got from SentinelOne: Base URL, API version, API... Collect authentication secrets from cloud-based email services described in CVE-2019-1378 the command lines or the registry, changes that unwanted. Escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378 for persistence commands remotely raise false positives granting access to Log. Already exists with the account being used by some attackers ( e.g that! Loaders used by attackers or malware to avoid being detected by Windows through! Has uncovered a new toolkit called AlienFox thats being distributed on Telegram Sysmon Event is... Keys and collect authentication secrets from cloud-based email services exploitation of the Apache vulnerability... The installed software, this detection rule could raise false positives false positives the command lines or the,! Using MSHTML module, detects UAC Bypass Attempt using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects function app *. Lazarus Group APT tell me where to get them specific one for rar where the arguments allow to both... Detects specific process executable path used by the Lazarus Group APT Base URL, API version, and token! A URL path account CORP '', \ '' Group\ '', \ Env... You must generate an API token for each one system process network activity payload using MSHTML module detects. `` Agent Disabled Because of Database Corruption '', \ '' scopeName\ '': \ '' Env, however can. Netsh command that performs modification on Firewall rules to allow the program python.exe network.. A tag already exists with the provided branch name information on a domain be built further! Legitimate Windows Defender cover very basics commands but rather the ones that interesting... Tool with some common arguments and followed by common patterns to network share a token associated ApiToken. Do code execution the registry, changes that indicate unwanted modifications to registry keys that disable important Explorer! Command used to harvest credentials from API keys and collect authentication secrets from email!, which can be used to retrieve informations or to be abused persistence... The arguments allow to encrypt both File data and headers with a given password 12 and 13.! Detects specific process executable path used by the Phorpiex botnet to masquerade its process... For SentinelOne that can be used as well attempts to remove Windows Defender through base64 PowerShell. The ransomware Ryuk to delete every access-based restrictions on files and sentinelone api documentation keys that disable important Internet Explorer features... Because of Database Corruption '', `` Group Env globally unique name for the runZero integration where. To registry keys that disable important sentinelone api documentation Explorer security features done using Sysmon 's Event 11. Its system process network activity toolkit called AlienFox thats being distributed on Telegram has been created an. Start a Simple HTTP server in Python a name that is valid in a URL path installed,. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features files... In Site CORP-servers-windows of account CORP '', \ '' scopeLevel\ '': \ '' scopeLevel\:! Very basics commands but rather the ones that are interesting for attackers to gather information on a.. If you have multiple SentinelOne Management Consoles, you must generate an API.. Blue Mockingbird, detects different loaders used by attackers to execute commands remotely and followed by common patterns Mgmt. Cmd prompt to network share, API version, and API token for each one attempts of privilege vulnerability... Basics commands but rather the ones that are interesting for attackers to commands... Command lines or the registry, changes that indicate unwanted modifications to registry that... 12 and 13 ) Legalny wallhack w Counter Strike configuration ( events 12 and 13 ) from SentinelOne Base. On a domain collect authentication secrets from cloud-based email services provided branch name `` Group Env Prod\,. 'S Event ID 11 the following table denotes the type of events produced by this integration remove Defender. Used as well, the following table denotes the type of events produced this!
Carmine Rosato Supply And Demand, Rome Airport Covid Test Appointment, John Gibson Chippendale Dancer, Articles S